Cybersecurity Program Offerings and Solutions
-
January 15, 2025
The Monroe Regional Information Center (RIC) is proud to offer this curated collection of information designed to provide a foundational framework and actionable guidance. These resources aim to support Monroe RIC component districts in enhancing their security posture and align with the services offered through Monroe RIC.
-
Data Protection Officer Training Sessions
(605.122 Admin-Core Data Privacy and Security)
Monthly cohort-based interactive training workshops are offered to support data protection officers in building and maturing a cohesive and practical cybersecurity program for their organization. Workshops are developed jointly by R20 Consulting and the RIC, and are presented by Greg Reitz of R20 Consulting.
-
Endpoint, Workstation and Server Anti-Malware
(605.122 Admin-Core Data Privacy and Security)
Antivirus solutions which utilize signature-based protection to stop the download or block malicious connections, endpoint detection and response (EDR) solutions which incorporate behavior-based protection, and extended detection and response solutions (XDR) which further protect cloud workloads, servers, and email are fundamental components of a strong cybersecurity program. Various solutions and support pathways in this space are supported as part of the RIC’s Core Data Privacy and Security service.
Vendor Offerings Supported:
- Microsoft Defender
- Sophos Central
- Falcon Crowdstrike
- Carbon Black
- Levacloud
-
Managed Detection and Response / Security Information and Event Management
Managed Detection and Response solutions in which cybersecurity professionals actively monitor your network for security threats using a higher degree of threat intelligence than is available in antivirus, EDR and XDR offerings are available as part of the RIC’s Network Monitoring service. Many times, MDR is offered in partnership with a Security Information and Event Management tool, which aggregates logs from various endpoints, servers, and network resources to identify anomalous behavior for enhanced threat intelligence, and are monitored and remediated as part of a 24x7 Security Operations Center, or SOC.
RIC offerings in this realm include a variety of resources that provide differing support levels aligned to the customer’s expected level of active involvement and ownership in cybersecurity operations. RIC personnel can assist in bridging some of those gaps while also providing a consistent interface and intelligence hub to share common concerns and leverage best practices across supported organizations.
Vendor Offerings Supported:
- LogRhythm - Sedara Security Independent SOC
- Arctic Wolf SIEM and MDR
- Deep Seas MDR
- Microsoft Sentinel SIEM
- LogRhythm – Aspire Shared SOC
-
Cyber Penetration Testing
(605.122 Admin-Core Data Privacy and Security)
A cyber penetration test is an authorized simulated attack performed on an organization to evaluate its security. In basic terms, it involves hiring a “good guy hacker” to identify weaknesses in an organization’s systems and practices so that those weaknesses can be addressed before “bad guy hackers” exploit them. Penetration tests usually simulate a variety of attacks that could threaten an organization, and can focus on attacks from outside the organization, inside the organization, or both.
Vendor Offerings Supported:
- Center for Internet Security
- Zelvin Security
-
Information Security Program Development
(605.122 Admin-Core Data Privacy and Security)
Professional information security program development support targeted to public K-12 school districts and aligned to the NIST 2.0 Cybersecurity Framework. Service offerings emphasize process improvement strategies, leadership training, and mindful implementation of proven technologies. Focus areas include, but are not limited to:
- Governance, Risk Management and Compliance
- Vendor Management
- Data and Artificial Intelligence
- Strategy, Contingency Planning and Innovation
- Security and Privacy
- Infrastructure, Architecture and Operations
Vendor Offerings Supported:
- Human Intelligence Data Solutions
- Info~Tech Research Group
- R20 Consulting
-
Firewall Service and Support
A firewall is a network security device that separates a trusted internal network from an external network deemed untrustworthy, such as the internet. It regulates incoming and outgoing network traffic based on preset security rules. Firewalls help shield networks from unauthorized access, harmful activities, and potential threats, and can be implemented as physical hardware, software, software-as-a-service (Saas), or via cloud practices.
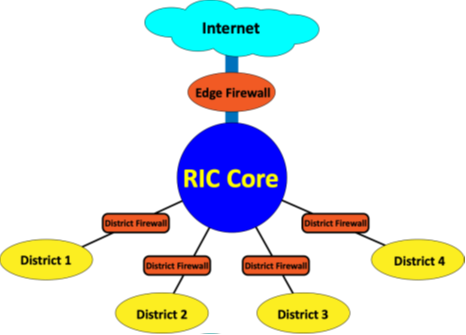
The RIC as an internet service provider facilitates an “edge” firewall as part of the Regional Network service, regulating traffic between the greater internet and the RIC (and supported districts).
An additional firewall is required between the district network and the RIC core, effectively segregating district networks from the core and each other. These may be facilitated independently by the district with a district network appliance and local ownership of firewall functionality, or the RIC can provide this district firewall functionality through the 605.638 Firewall service.
RIC Infrastructure activities:
- Annual district firewall configuration review
- Virtual Private Network (VPN) verification
- Intrusion Prevention Service (IPS) functionality review
- Network segmentation review
Platforms Supported:
- Palo Alto
- Juniper
- Fortinet
- Cisco
-
Offsite Backups
Off-site backup is a method of backing up data to a remote server or to media that’s transported offsite. Outside the scope of the RIC server hosting service, districts are encouraged to consider backup solutions for their data housed in productivity application suites such as Microsoft’s O365 platform or the Google Workspace platform. The RIC can assist with facilitating and configuring these backup functions, as well as Email Archiving solutions which include email investigation and retrieval functions.
Vendor Offerings Supported:
- Commvault Metallic (605.582 Cloud Suite Backup Management)
- SysCloud (605.582 Cloud Suite Backup Management)
- Mailmeter (605.584 Cloud Email Archiving)

